All product names, logos, and brands used in this post are property of their respective owners.
Out of the box, the Duo Authentication Proxy service (which is responsible for Duo Directory Sync) provides a couple of options to selectively synchronize users from an on-premise directory to the Duo cloud:
- Filter by Base DN in the directory configuration
- Select specific groups to synchronize in the directory configuration
These options usually suffice, but what if your directory has bad data that you have no control over? For instance, a perfect programmatically maintained Active Directory group exists that contains all of the users you want to synchronize to Duo but there are 1-2 application accounts in the same group that you DO NOT want to sync (but cannot remove from the group for legacy reasons).
Instead of creating and maintaining an entirely new group, you can deny permission to specific AD users and nested groups, effectively hiding them from the Duo Authentication Proxy service (without removing them from the AD group or Base DN scope). This prevents the auth proxy from reading or synchronizing them to Duo.
Admittedly, the dsacls command (part of Remote Service Administration Tools) is a little old school, but it was my path of least resistance because of my familiarity with it. You can achieve the same result manually in Active Directory Users and Computers (ADUC) and I suspect there is a more modern, PowerShell based approach out there too.
PowerShell
The general syntax of the dsacls command for adding a Deny permission for an Active Directory object (a computer in this case) to another AD object (a user or group in this case) is as follows:
dsacls 'DN of unwanted user or group' /D 'DOMAIN\COMPUTER$:GA'
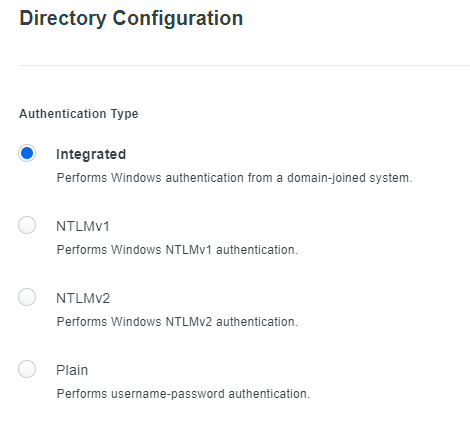
In the following examples, the domain name is “CONTOSO” and the server running the Duo Authentication Proxy Service is “DUOAP01.” They also assume your Auth Proxy/Directory Sync process is configured using Integrated authentication:
By using dsacls to Deny Full Control permission by the Duo Auth Proxy server to a specific user or group, the user or group is excluded as a one-off from the Duo Active Directory Sync process.
dsacls 'CN=legacyapp,OU=Users,DC=contoso,DC=com' /D 'CONTOSO\DUOAP01$:GA'
dsacls 'CN=DuoExcludedGroup,OU=Groups,DC=contoso,DC=com' /D 'CONTOSO\DUOAP01$:GA'
Executing these commands would exclude the user “legacyapp” and the group “DuoExcludedGroup” from Duo AD Sync via the Authentication Proxy service.
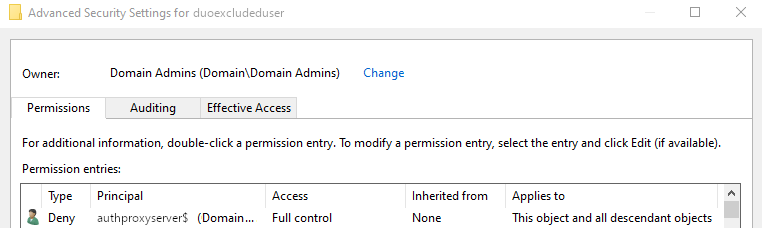
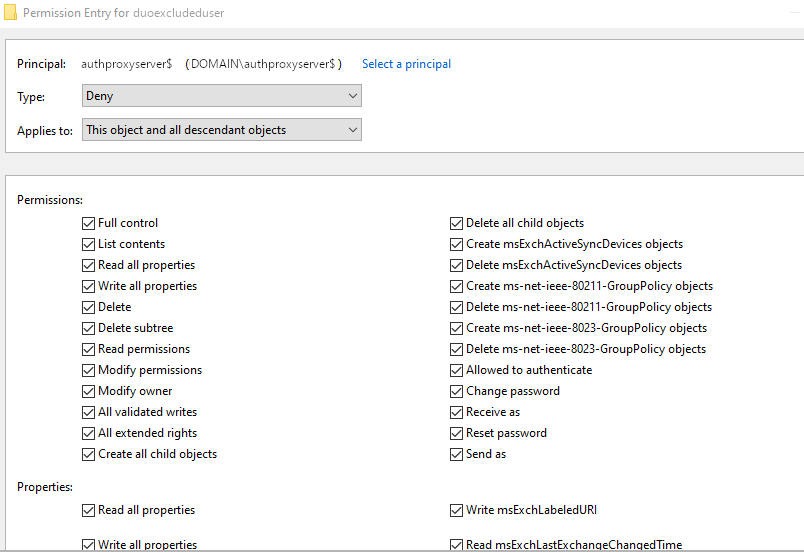
You can confirm the Deny permission using the Security tab on the user or group object in Active Directory Users and Computers (ADUC):
Note, if your Auth Proxy / Directory Sync process is configured using NTLMv1, NTLMv2, or Plain authentication, a similar deny process applies. Instead of denying full control to the Auth Proxy server’s computer account, you would deny access to the user account specified in service_account_username in the [cloud] section of the Authentication Proxy configuration.
Command Prompt (CMD)
The syntax in good ole command prompt (cmd) is almost identical to PowerShell. It is a matter of swapping the single quotes (’) for double quotes (").
dsacls "DN of unwanted user of group" /D "DOMAIN\COMPUTER$:GA"
If you do not, dsacls throws an error like this:
The parameter is incorrect.
The command failed to complete successfully.
Closing thoughts
This approach is not incredibly sustainable at scale, but I hope it helps someone in a pinch.