
All product names, logos, and brands used in this post are property of their respective owners.
As of late 2019, the original Flow SFTP connector is deprecated in favor of the new Power Automate SFTP - SSH connector. There are configuration and functional differences between the old and new connectors. This post was revised in late 2019 to reflect and capture the changes.
The SFTP - SSH connector in Microsoft Power Automate (Flow) has quickly become my personal favorite. It is quite robust - I am most pleased with its support of SSH key-based authentication and SSH/SFTP ports besides 22 (the default). In light of this, I wanted to share some of my findings in hopes they will be of value to someone else.
Quick tips
Read on for more detailed information about these tips - they apply to the SFTP - SSH connector:
- Ensure you are using the correct credentials
- Ensure PowerAutomate can resolve your SFTP server’s hostname using DNS
- Allow MS Power Automate’s (Flow’s) source IP addresses through your firewall
- Ensure your private key is PEM (OpenSSH) formatted (and NOT PuTTY Private Key File / .ppk formatted)
- If using SSH host key fingerprint validation, ensure the finger print is formatted properly (MD5)
Error messages and meanings
The “SFTP - SSH” connector (in my experience) does not provide incredibly meaningful error messages in the user interface (although this is improving over time). It generally throws a single error message when creating new SFTP connections if something is amiss.
The general SFTP connector error:
Test connection failed. Details: BadGateway
Thanks to an incredible tip from ScottB, I recently learned that additional details about the generic “Test connection failed. Details: BadGateway” error are available in the asynchronous HTTP conversation between the PowerAutomate web front end (UI) and backend.
To view the more detailed error messages, you can do the following:
Download and install the free Fiddler Web Debugging Proxy by Telerik (one of my favorite tools)
Close all browsers and other applications, then run Fiddler
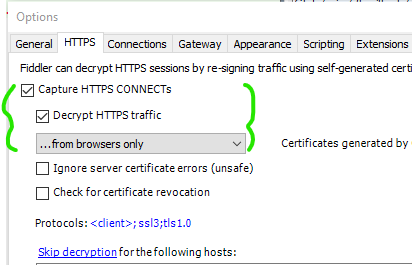
Under the Tools menu, select Options and the HTTPS tab
Configure the “Decrypt HTTPS traffic” option as follows (accepting the prompts to install the Fiddler certificate)
Browse to your flow in PowerAutomate and add/update your SFTP - SSH connector, reproducing the “BadGateway” message
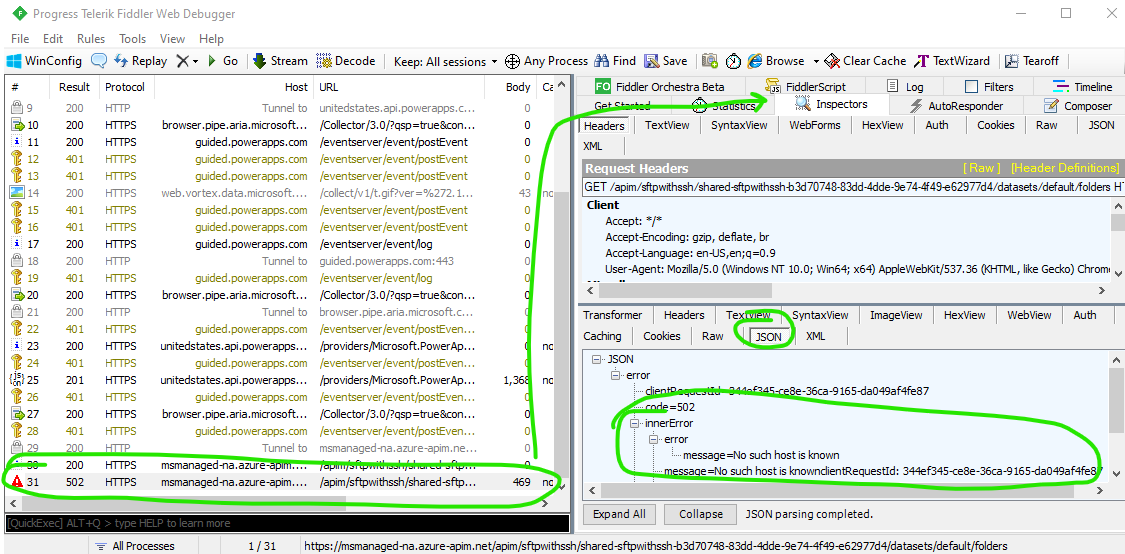
Review the HTTP trace in Fiddler and look for failures (usually HTTP 400, 502, or 504 errors) - select the failed request, then click Inspectors and JSON in the response section - this will reveal a more detailed error message
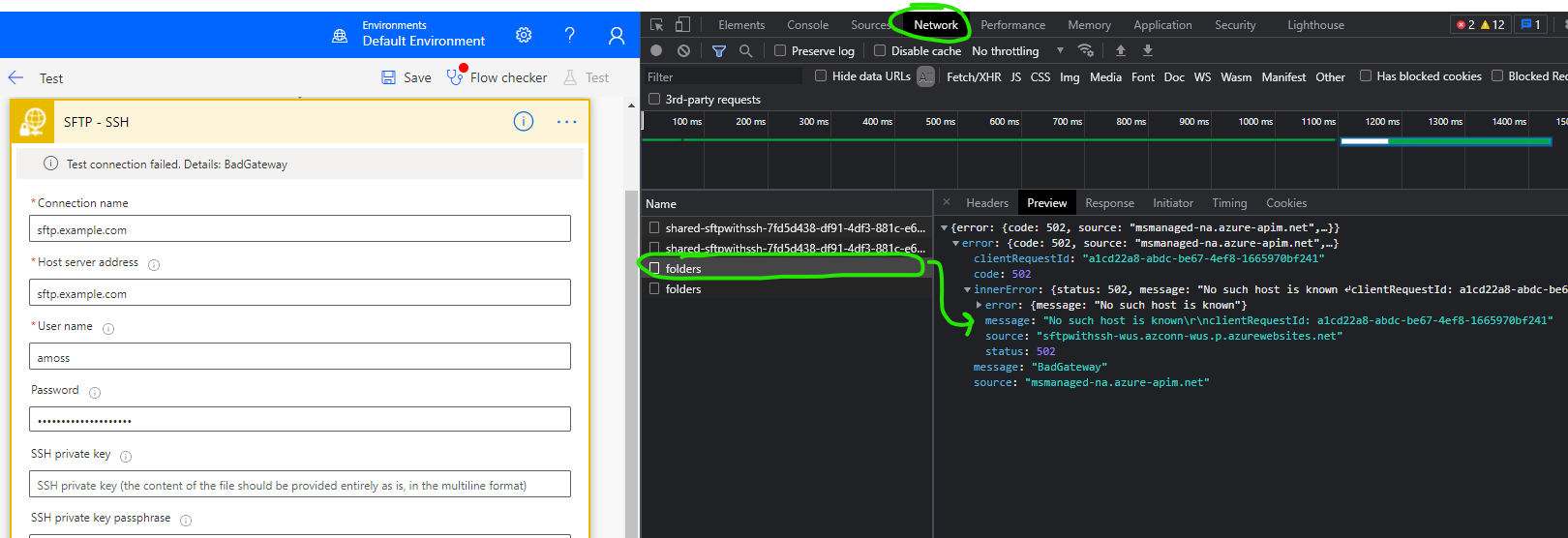
If using Fiddler is not desirable, you can also use your browser’s built-in Developer Tools (thanks to Jens for pointing this out) to capture the same diagnostic information. This eliminates the need to download, install, and configure a separate tool.
In this post, I’ve detailed some of the possible causes of the generic message and the more specific error messages that can be captured in the HTTP conversation. I have also added an appendix to the end of this post with the legacy Flow “SFTP” connector error messages and causes.
Credential issues
Symptoms of Flow being unable to access your SFTP server due to a bad username or password include the following error message in an HTTP trace:
message=Permission denied (password).
If you encounter this message, ensure your credentials are correct.
DNS (name resolution) issues
Symptoms of Flow being unable to access your SFTP server due to a failed hostname lookup (DNS) include the following error message in an HTTP trace:
message=No such host is known
If you encounter this message, ensure your SFTP server hostname is correct and has fully propagated in public DNS (or use an IP address instead).
Firewall issues (allow IPs and IP ranges)
If you allow open access to your server via port 22, this may not concern you. However, if you restrict SSH or SFTP access via software (i.e. iptables) or hardware firewall, read on.
Symptoms of Flow being unable to access your server due to a firewall issue include the following error message in an HTTP trace:
message=A connection attempt failed because the
connected party did not properly respond after a period
of time, or established connection failed because
connected host has failed to respond
MS Power Automate’s (Flow’s) source IP addresses are documented in a post entitled Managed connectors outbound IP addresses. Review the addresses and IP ranges under Power Platform and ensure your firewall rules are up to date.
The source addresses change over time. Ideally, there would be a way to obtain these IP ranges programmatically (via web service - like this for O365). As of December 2019, that is not the case. My only advice is to use a service like ChangeTower to monitor for changes to the Managed connectors outbound IP addresses page and manually update your firewall when Microsoft updates the IP list. Or, submit feedback through the Feedback web portal and ask that Microsoft add PowerAutomate/Flow to the Office 365 IP Address and URL web service.
SSH Key Authentication
If you are familiar with SSH key authentication, configuring this in MS Power Automate (Flow) is relatively easy. A caveat is that the private key you paste into the Power Automate interface must be PEM formatted (specifically, PKCS#1 and NOT PKCS#8 nor OPENSSH). Many thanks to Sam Giffney for discovering and pointing that out. The PEM/PKCS#1 format is a contrast to the deprecated “SFTP” connector which required a PuTTY Private Key File (.ppk) formatted key.
Consider the following if you receive this detailed error in an HTTP trace:
message=Permission denied (publickey).
Ensure your key is in fact PEM (PKCS#1) formatted and paste that into the SSH private key field in your flow. Even though the SSH private key field appears to be a single line of text, it will accept the entire PEM formatted private key:
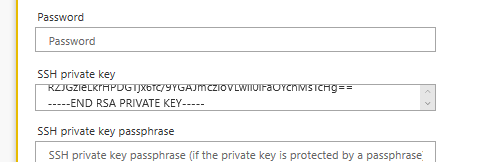
The following are truncated (…) examples of PKCS#1 (PEM) SSH-2 private key which WILL work in Microsoft Power Automate (Flow) with the “SFTP - SSH” connector:
DSA private key, no passphrase
-----BEGIN DSA PRIVATE KEY-----
MIIBuwIBAAKBgQDc9i6f4x4Xw8/ZOb0AUqRd/Wb8PKrjvywHyPtP445a4RIxcU7a
.
.
.
-----END DSA PRIVATE KEY-----
DSA private key, with passphrase
-----BEGIN DSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,4FE4ED2732CEBC1E7674936B31D1097B
RlTNQXX/PTngIMyyXOgD3WZ38lFxgi+cVBO9eclYZsHuc28dMTae4xkza2FkPst8
.
.
.
-----END DSA PRIVATE KEY-----
RSA private key, no passphrase
-----BEGIN RSA PRIVATE KEY-----
MIIEpgIBAAKCAQEA0hmlr0tjRj3XG6O1nhrUecyor7c0hImWgeCaFqkXoCKX4jDd
.
.
.
-----END RSA PRIVATE KEY-----
RSA private key, with passphrase
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,00F5C6BA7EF2F0B51399EBB39C9E3A8C
QJMIm4Lfm3xeBwY6bMPt2UVnLyDdHeBvmpn7gLplowK4m/0q5oOKXd3IVg6skInB
.
.
.
-----END RSA PRIVATE KEY-----
ECDSA private key, no passphrase
-----BEGIN EC PRIVATE KEY-----
MHcCAQEEIAWQPfv0gTZAgNCd7vWM9Fxp/ameRjFGEgbGf/urIvQCoAoGCCqGSM49
.
.
.
-----END EC PRIVATE KEY-----
ECDSA private key, with passphrase
-----BEGIN EC PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,9BBF5A4BBD0D30FB8625CB3D7F4F7E25
V65imHuCjBKf6s2wSvqTMefSZgNRMzSDI+3/mHVJmM1aSYjIDpo3MLCW2D4DjZak
.
.
.
-----END EC PRIVATE KEY-----
The following are examples of keys in other formats which WILL NOT work in Power Automate (Flow) with the “SFTP - SSH” connector:
PuTTY (PPK) private key
PuTTY-User-Key-File-2: ssh-rsa
Encryption: none
Comment: imported-openssh-key
Public-Lines: 6
AAAAB3NzaC1yc2EAAAABIwAAAQEApnzCa10mgFV8F6Fe+i7FItcer/OcY/pXUia8
.
.
.
Private-Lines: 14
AAABAQCAbt8fn6Fbr6jfB3UnZeiIl1Iv9nFUcKnDB/DPT7SR7x32EHOZyhsELWtL
.
.
.
Private-MAC: 9030568136067ba5f327ba6652452f217f19770d
PKCS#8 formatted private key (note the lack of “RSA”, “DSA”, or “EC” in the header/footer)
-----BEGIN PRIVATE KEY-----
MIIEvgIBADANBgkqhkiG9w0BAQEFAASCBKgwggSkAgEAAoIBAQDBZ6DFsRqOrY8I
.
.
.
-----END PRIVATE KEY-----
OPENSSH formatted private key (note the lack of “RSA”, “DSA”, or “EC” in the header/footer)
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAaAAAABNlY2RzYS
.
.
.
-----END OPENSSH PRIVATE KEY-----
If you are using a pass-phrase with your SSH key, the following message indicates a pass phrase specific issue:
message=Invalid data type, INTEGER(02) is expected, but was 9D
Resume Capability and its Functionality
This is leftover from the deprecated Flow “SFTP” connector (which was based on WinSCP). The new “SFTP - SSH” connector in Power Automate no longer relies on WinSCP and as such, no longer offers “resume capability.”
SSH Host Key Finger-print Validation
If you leave SSH host key finger-print validation enabled (recommended), ensure you provide the SSH Host Key Finger-print in the correct MD5 format. An incorrectly formatted host key fingerprint will generate this error when creating a connection:
Test connection failed.
Details: The provided SSH host key finger-print format
is not supported. It must be in 'MD5' format.
There are a plethora of ways to obtain your server’s host key fingerprint. Since I use WinSCP for other tasks, that is my method of choice. Connect to your server using WinSCP, then open the Session menu and select the Server/Protocol Information item.
Copy/paste the value displayed:
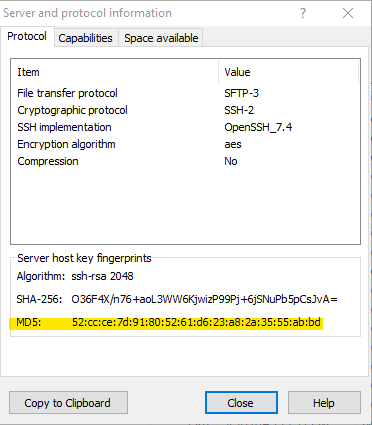
For the ssh-rsa algorithm:
CORRECT (example):
52:cc:ce:7d:91:80:52:61:d6:23:a8:2a:35:55:ab:bd
INCORRECT (example):
ssh-rsa 2048 52:cc:ce:7d:91:80:52:61:d6:23:a8:2a:35:55:ab:bd
If the finger-print you supply is simply incorrect (does not match the destination host’s fingerprint), the following error is thrown by the Power Automate (Flow) “SFTP - SSH” connector:
Test connection failed.
Details: Key exchange negotiation failed.
The detailed error message (from a Fiddler trace) is as follows:
message=Key exchange negotiation failed.
Content type and encoding issues
Some SFTP - SSH connector actions (example: Get file content) contain an “Infer Content Type” setting. The default value is Yes (or True), which results in Power Automate “guessing” the content type of the file in question. In many cases, that is fine, BUT if the content looks like text, Power Automate always assumes it is UTF-8 encoded (even if it is something different, like ANSI / Windows-1252). The result can be garbled, incorrect characters (as Patrick H. discovered - see comments).
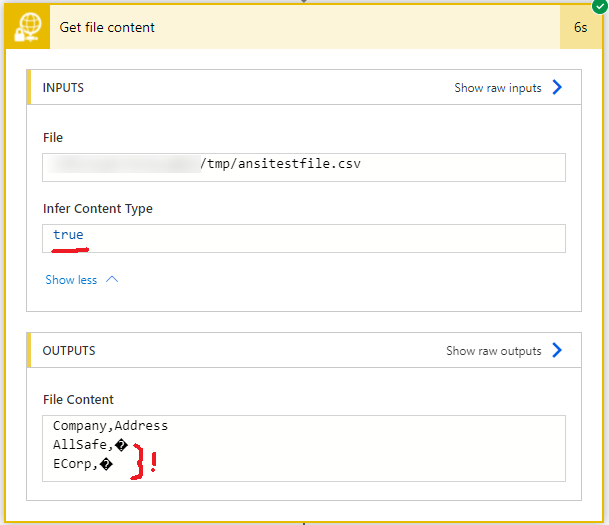
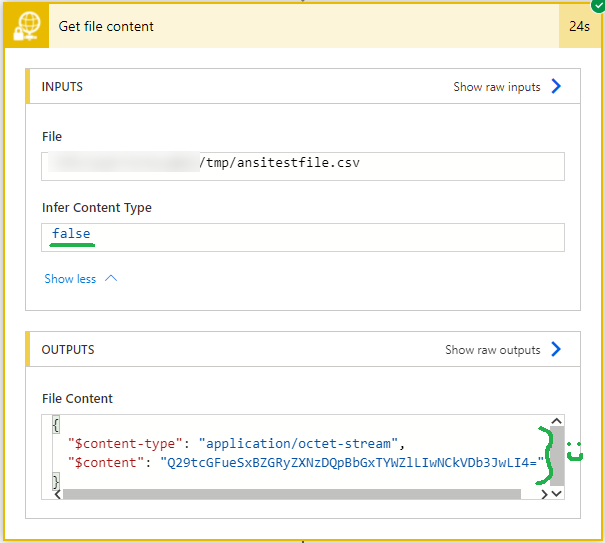
To work around that and force Power Automate to treat text content as binary (base64 encoded), set “Infer Content Type” to No. That preserves the text file’s encoding.
Permission issues
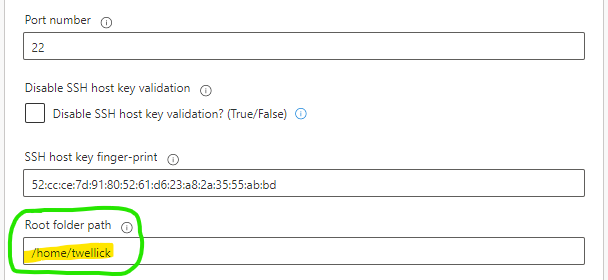
If the SFTP server you are connecting to is not using a chrooted jail AND the “Root folder path” is not specified when creating the SFTP - SSH connection in Power Automate, the following error may occur:
Test connection failed.
Details: Permission denied
In that scenario, the connector defaults to the “/” path on the SFTP server, to which the user may not have access. Thanks to Melanie for pointing that out - see comments. In some cases, you can work around the issue by specifying a “Root folder path” on the SFTP server that your SFTP user has access to (during connector setup):
Appendix: legacy “SFTP” connector error messages and causes
The deprecated “SFTP” connector threw a variety of error messages, depending on the situation. Those are captured below for history’s sake. Note that these error messages DO NOT apply to the “SFTP - SSH” connector in Power Automate.
Flow/Power Automate unable to access your SFTP server due to a firewall issue:
Please check your account info and/or permissions and try again.
Details: Unable to connect to the remote server '...'.
Unable to connect to the remote server '...'. clientRequestId:...
Flow/Power Automate unable to access your SFTP server due to an SSH key or format issue:
Please check your account info and/or permissions and try again.
Details: Invalid SSH private key provided.
Invalid SSH private key provided. clientRequestId ...
Flow/Power Automate unable to access your SFTP server due to a host key fingerprint issue:
Please check your account info and/or permissions and try again.
Details: SSH host key fingerprint
'...' doesn't match the original one '...'.