
All product names, logos, and brands used in this post are property of their respective owners.
In this quick post, I will highlight a process to generate an OATH-TOTP credential in a YubiKey using YubiKey Manager for Windows (specifically the ykman.exe CLI) and PowerShell. The TOTP credential appears in Yubico Authenticator when the YubiKey is inserted and can be used with services that require you to provide your own OATH-TOTP secret (Duo, Azure MFA / O365, etc.).
I will use Duo Security to test the generated credential (token), and as a bonus, I will demonstrate retrieving YubiKey TOTP codes via the command line using PowerShell and ykman.
To use this example, you must have YubiKey Manager downloaded and installed. I used the default install path in my example.
The PowerShell script
I will be the first to admit that the mathematics behind OATH-TOTP and base32 conversion is a little out of my wheelhouse. I have infinite respect for the engineers and developers who devised these!
Based on some excellent code by others (noted in the script below), I assembled the following PowerShell snippet which generates a TOTP secret (in hex, then converts to base32) and uses the secret to create an OATH-TOTP credential in the YubiKey. To test with Duo Security, the YubiKey’s serial number and the hex representation of the secret are output as CSV. These PowerShell commands can be modified slightly to create TOTP base32 secrets for bulk administrator import into Azure AD (O365 or Azure MFA).
| |
Once the script runs, the new credential should appear in Yubico Authenticator when the tokens refresh (or when you remove and re-insert the YubiKey):
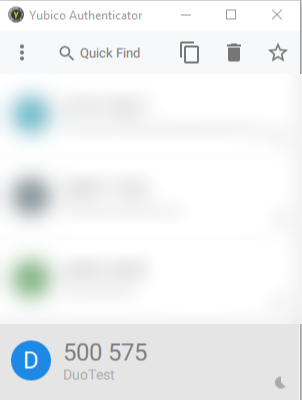
Be sure to take note of the comma-separated value output by the script - it will be imported into Duo in the next section:
> write-host "$serialNumber,$hexSecret"
6169235,c841ff5870e161da5d2f9e1af95962
Testing with Duo
I am a Duo fan and it provides a quick and frictionless way to test the token. Note that Duo does not support OATH-TOTP token drift or resync. This does not apply to YubiKey TOTP credentials though - that guidance applies to traditional hardware tokens (with their own clock). In the case of YubiKey, the “token” does not have its own clock. It simply securely stores the OATH-TOTP secret and relies on your computer or phone clock (via Yubico Authenticator) to generate the one-time passcode.
First, import the credential as a Hardware Token in the Duo Console (2FA Devices -> Hardware Tokens) as follows:
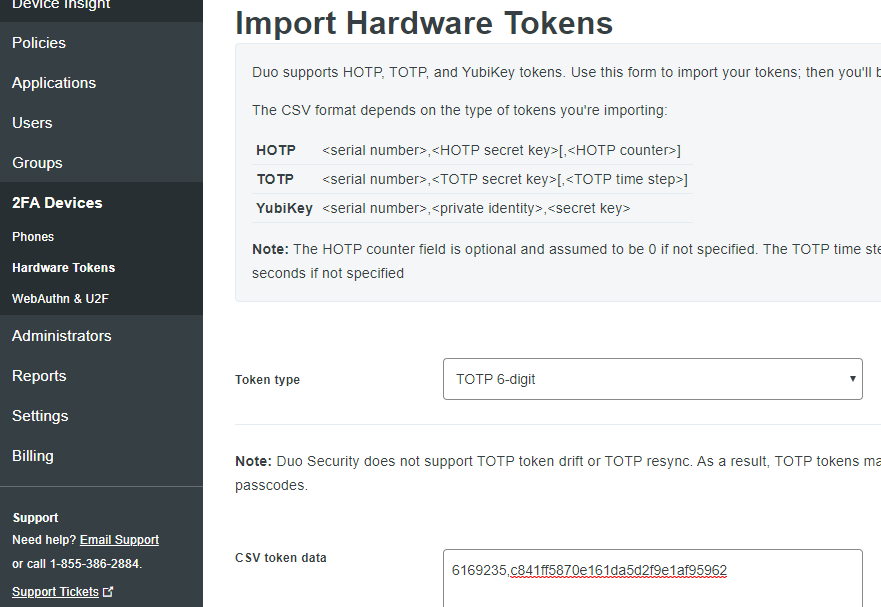
Ensure TOTP 6-digit is selected and paste the CSV line from the PowerShell script.
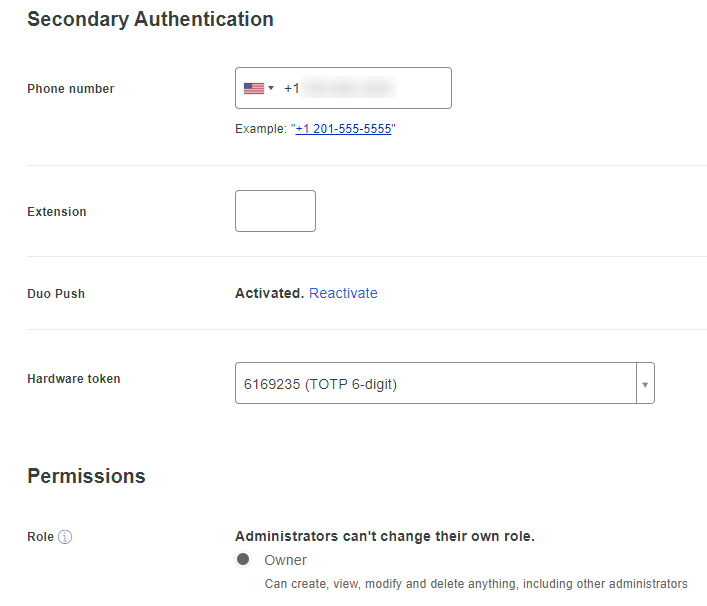
Then, attach the token to a user or administrator (I used my Duo admin account for the test):
Finally, logout and back into the Duo Console and provide the TOTP passcode in one of the following ways:
Yubico Authenticator
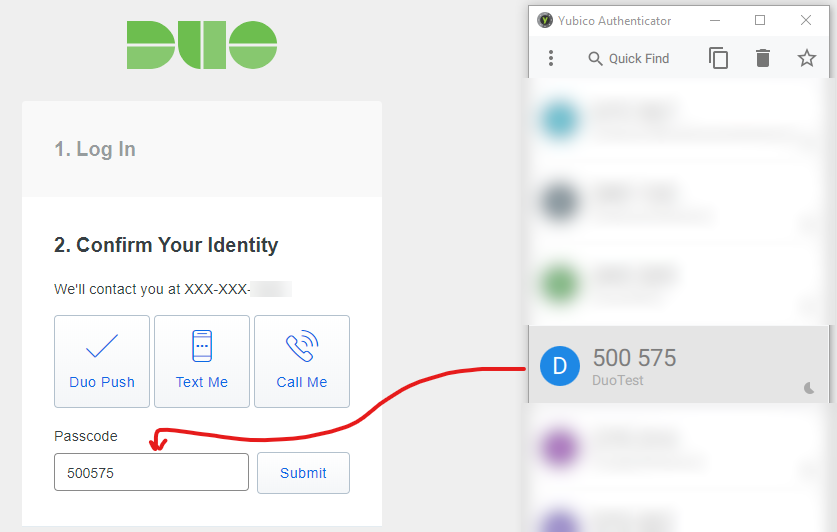
PowerShell (command line)
> ykman oath code "DuoTest"
DuoTest 500575
If all went well, you should be authenticated to the Duo console.