
All product names, logos, and brands used in this post are property of their respective owners.
In writing this, I hope I am not the only one who has encountered this scenario. You get the call or ticket: “Can you check the server CS30? It is not normal and performing strangely.” Being a diligent systems administrator, you log into CS30 to take a look. As the desktop background renders, you start to see warnings and notifications from your antivirus/antimalware solution: “infections detected, cannot be quarantined: Trojan.Emotet …” (or some other credential-stealing malware variant). Yikes! And you just logged in with your privileged account!
Probably best to assume your privileged credentials are now compromised or otherwise in the wild.

Although this specific scenario may not occur frequently, I feel it makes sense to change or rotate your privileged account password more often than you would other accounts. If you use a YubiKey (and the good old static password configuration), you can script the reset process with Powershell to save yourself some keystrokes, time and panic if you must reset your password in a hurry.
If you do not have a YubiKey already, you need one. Or two so you have a backup.
In this post, I will share a PowerShell based approach to quickly generate a new random, static password on a YubiKey and subsequently change your local or domain account password.
Install the YubiKey Manager (ykman) command-line interface (CLI)
It is worth noting, there are 2 YubiKey command line interfaces.
“YubiKey Personalization Tool” contains ykpersonalize.exe
“YubiKey Manager” which contains ykman.exe
There is some overlap between the tools but after the valuable comment (featured below) by Dag Heyman, the tool’s maintainer, I prefer using ykman.exe (YubiKey Manager) for simplicity.
There is an install for YubiKey Manager on Windows which includes ykman.exe by default - simply download the appropriate version from Yubico, run the installer and follow the prompts.
Use PowerShell to call ykman and generate a random, static password in your YubiKey
Under Windows, ykman does not require elevation to interact with the YubiKey. That being the case, I wanted to create a function or script I could run to quickly do the following:
Generate a random, static password in the YubiKey that complies with most password policy requirements (note: the generated portion should comprise only part of your complete password - more specifically, the end of it. For security, prepend a password of your choosing to the generated password to create a “something you know” and “something you have” scenario.)
Set the password on my local Windows or domain account to the new static password in the YubiKey
You can generate a new static password on the YubiKey with these PowerShell commands (via ykman):
| |
If you run the sample above, you should end up with a random, 16 character password generated on your YubiKey in configuration slot 2. You can long-press the button to release and view the password (assuming you used configuration slot 2 as I did).
To flesh things out further, I put together this snippet.
It uses the base logic of the original command to generate a new static password on the YubiKey, then reset the password of the user running the PowerShell session to the new static password (requires pressing the button on the YubiKey to release it twice).
| |
Once done, the account password is reset and you can login by typing your personal password, then long pressing the button on your YubiKey to release the generated password.
For a more detailed look at the construction of a secure, static password on YubiKey, see:
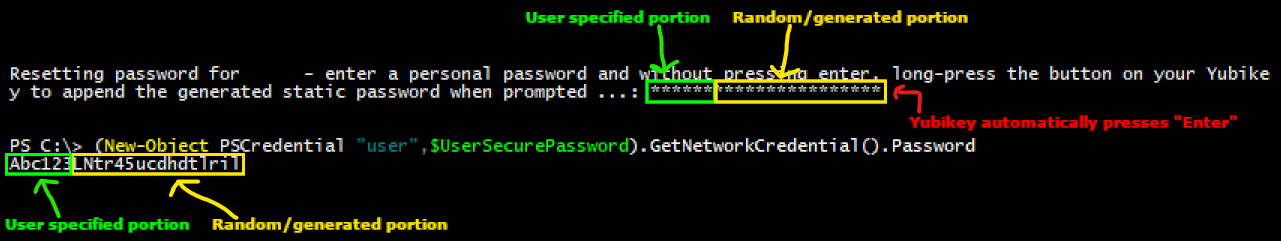
In this example, the personal portion (something I “know”) of the static password is Abc123. The random (generated) portion of the static password is LNtr45ucdhdtlril (something I “have” - this is emitted from the YubiKey).
Closing thoughts
In case you are curious, a static password can be generated in the YubiKey using ykpersonalize (YubiKey Personalization Tool) as follows:
| |
The magic with ykpersonalize comes from the -a switch - this specifies a “randomness source” in the form of a hex AES key that the YubiKey uses to generate the static password. Supply a different hex key to ykpersonalize each time you run it to generate a unique password each time. If you fail to specify an AES key (-a), ykpersonalize will throw an error like this:
YubiKey personalization error: no randomness source available
Speaking of which, the $RandomHex variable is generated based on the awesome work of Forty3 from Code Golf on Stack Exchange. I made a minor adjustment to Forty3’s PowerShell code that generates a random uuid string.
As you may have guessed, I actually started with ykpersonalize first but now prefer ykman because the latter eliminates the need to generate a randomness source (hex) in PowerShell.
It is worth noting, static passwords on the YubiKey are not the most secure authentication option. Be that as it may, I have found that the convenience and versatility of static passwords outweigh the risks. I would argue that frequently changing or rotating static passwords (concatenated with your own secure password) on the YubiKey offers added protection to this approach.
Here are a few examples of where YubiKey static passwords shine:
- Across platforms and devices (Windows, macOS, Linux, etc.)
- Physical servers in a datacenter (with USB ports)
- Virtual servers via SSH, RDP, VNC, etc. access
- The VMware Remote Console (no copy/paste)
- Windows UAC (User Account Control) elevation screens (no copy/paste)
- Broken devices where smartcard authentication, FIDO, etc. are no longer working properly
- Air-gapped devices with no network access
- “Chained” sessions where clipboard redirection does not work (i.e. VNC session running within an RDP session…do not ask)
In other words, YubiKey static passwords work anywhere a keyboard would, which is VERY flexible.
However you choose to proceed, stay secure (or at least more secure than your slowest friends) to avoid being eaten by the compromised credential bear!